Financial Services: DevSecOps Engineering
Checkmarx SAST
Checkmarx's Next Gen-SAST Engine Gives You Both Speed & Security
Learn MoreCheckmarx One
Static Application
Security Testing (SAST)
Checkmarx’ next-generation SAST combines both speed and security to improve your developer experience – with up to 90% faster scans and 80% lower false positives.


























What makes the Checkmarx SAST Solution Different?
There’s no need to choose between code scan speed and security in a single solution. Get the best of both worlds by streamlining your security testing while also securing mission-critical enterprise applications.
Adaptive Vulnerability Scanning
Scans quickly to find the most relevant results, while also identifying maximum risk for mission-critical applications.
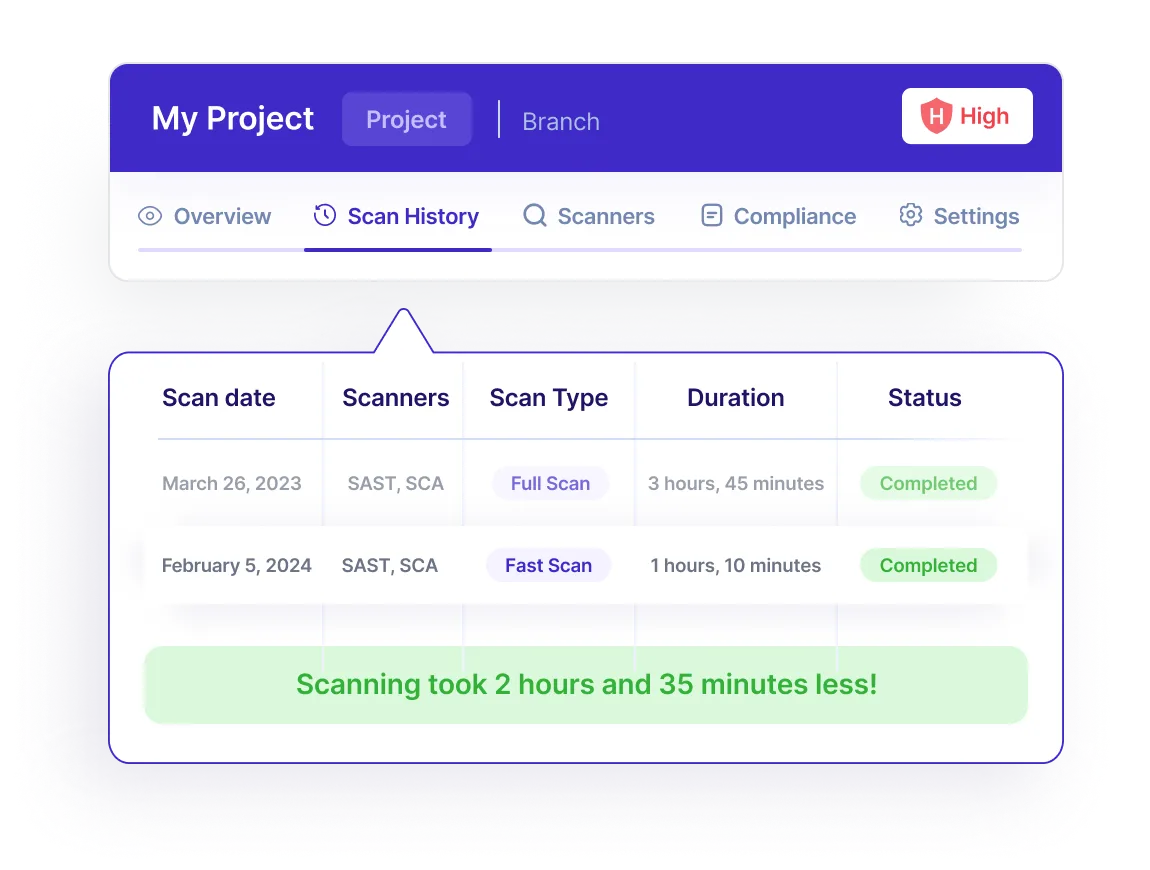
Best Fix Location
Get at the root of a vulnerability. This allows you to identify the best place to fix one line of code and remediate multiple vulnerabilities at once, for the greatest impact.
AI Query Builder
Use the power of Generative AI to better tune your SAST and improve result fidelity. AI Query Builder generates new, and customizes existing, queries to better tailor searches. No previous knowledge required.
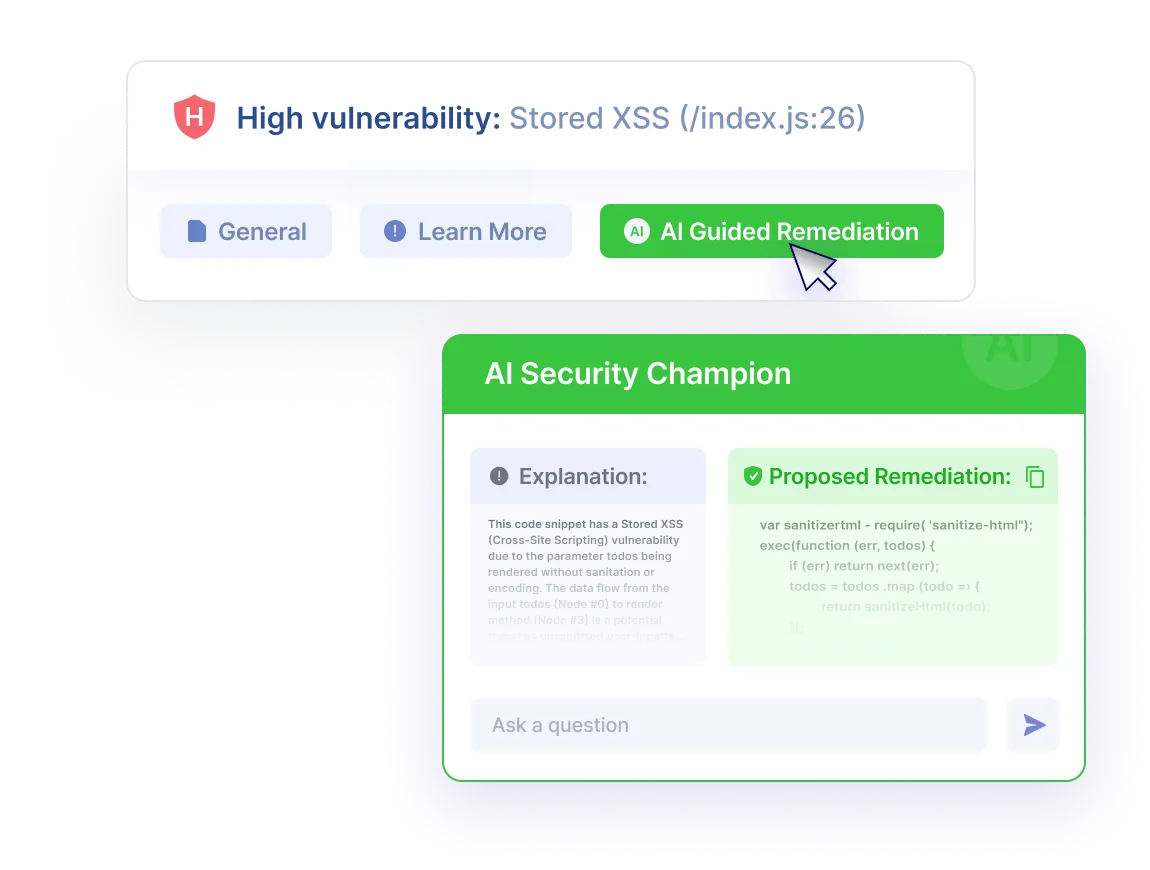
AI Security Champion
Generative AI recommends how to remove vulnerabilities in your application. AI Guided Remediation explains the vulnerability and how to remediate it.
Scan Uncompiled Code
Checkmarx SAST scans on check-in, directly from source code repositories including GitHub, GitLab, Azure, and Bitbucket, allowing it to integrate directly into your SDLC.
Wide language and framework coverage
Checkmarx SAST supports over 35 languages and 80 language frameworks, from the newest to legacy languages, promoting multi-platform development.
With Checkmarx SAST, You’re In Charge
Avoid a false sense of security with thorough, customizable scans that reduce noise
and prevent vulnerable code getting to production.
Solutions that build #DevSecTrust
Checkmarx SAST is trusted by enterprises around the world to empower their entire organization to create innovative and secure applications.
Ultra-fast Speed, Unparalleled Security
Get the best of both worlds. Discover the most relevant results quickly or take a deep dive into your mission critical apps. Secure your entire application footprint while fostering a better developer experience.
PrioritizeYour Findings With Accurate Results
Avoid false positives and false negatives with custom presets and queries, while receiving optimization guidance from our professional services experts, who will guide you every step of the way.
Develop Secure Applications Easily
Meet your developers where they are. Checkmarx SAST seamlessly integrates directly into developers preferred work environment, which allows them to see where and how to fix vulnerable code.
Save Time Fixing Vulnerabilities
Remediate vulnerabilities faster by only scanning the changed code. There’s no need to rescan an entire application every time.
Manage,Triage, and Fix Vulnerabilities Faster
Improved analytics and dashboards provide a holistic view of your AppSec posture, ensuring stakeholder alignment. Slice and dice the data to quickly spot anomalies and efficiently analyze vulnerabilities.
What Our Customers Say
Customers who chose Checkmarx over others
“Checkmarx One definitely checks all my boxes from a security standpoint and has a great interface that’s engaging and easy to use. Some of the solutions we considered were more complicated. With Checkmarx One, it’s easy to get right to the problem with little to no learning curve.”
Cybersecurity and Networking Manager
The Forrester WaveTM: Software Composition Analysis, Q2 2023
"After reviewing the Checkmarx platform, I’m not sure how Veracode is able to exist while being at a similar price point."

Cybersecurity and Networking Manager
“Incorporating Checkmarx's technology has revolutionized our development culture. It's more than just technology; it serves as the foundation of our security strategy, ensuring that our applications are secure by design.”

Sr. Director, Product Security Engineering

The Forrester WaveTM: Software Composition Analysis, Q2 2023
“The success of our AppSec program can be directly attributed to the tooling, processes and support provided by Checkmarx managed services. Our mission revolves around providing secure and compliant lottery and gaming applications and services to our clients around the globe, and with Checkmarx SAST, SCA and associated components enhanced by their stellar service support, we deliver on this promise with confidence and certainty.”

Head of Information Security

The Forrester WaveTM: Software Composition Analysis, Q2 2023
“After nearly nine years of using Checkmarx's SAST, CGI's journey has been one of seamless integration and consistent satisfaction. The last three years have been particularly smooth, reflecting the solution's reliability and our successful partnership.”

Lead Security Analyst

The Forrester WaveTM: Software Composition Analysis, Q2 2023
"Checkmarx’s execution is impressive; it’s brought all the products under one cloud platform"

Cybersecurity and Networking Manager
The Forrester WaveTM: Software Composition Analysis, Q2 2023
"By Far The Best AppSec Tooling Decision We Have Made!!"

Cybersecurity and Networking Manager
The Forrester WaveTM: Software Composition Analysis, Q2 2023
"We were thrilled to find Checkmarx, which helped us improve the SLA for identifying and remediating risk, reduce risk and the number of vulnerabilities, and eliminate high- and meduim-risk issues."
Tech Lead, Red Team/DevSecOps
The Forrester WaveTM: Software Composition Analysis, Q2 2023
"Checkmarx made security team and developers life easier."

IT Services
The Forrester WaveTM: Software Composition Analysis, Q2 2023
Frequently Asked Questions
Checkmarx’ SAST tool is part of the Checkmarx One platform. This allows a complete enterprise application security program to run on a single platform, reducing total cost of ownership and allowing for correlation and better actionable insights.
The Checkmarx One platform includes:
Checkmarx SAST supports over 50 programming languages and 80 development frameworks out-of-the-box. The full list of supported languages and frameworks is listed in our documentation.
Professional Services can help accelerate value faster. This starts with our AppSec Program Methodology & Assessment (APMA) Framework, which helps provide actionable steps to improve your AppSec maturity.
Professional Services can also help you optimize your solution to focus on finding exploitable vulnerabilities, as well as providing training, managed services, and more to be a partner in your AppSec journey.
You can explore all Checkmarx’ documentation on the documentation page.
CxSAST is on-premises, while Checkmarx One is our enterprise cloud-native platform.
Both CxSAST and SAST on Checkmarx One use the same SAST engine.
Find Critical Vulnerabilities In Your Applications
Checkmarx SAST shows you exactly what critical vulnerabilities to fix, and gives you the flexibility to create and deliver secure applications.
What CISOs say about Checkmarx
Customers who chose Checkmarx over others

PCL Construction

PCL Construction

PCL Construction
“With Checkmarx One, it’s easy to get right to the problem with little to no learning curve”

Joel Godbout
Manager, Cybersecurity and Networking | CISSP
Checkmarx One: The Enterprise Cloud-Native Application Security Platform
Checkmarx One delivers a full suite of enterprise AppSec solutions in a unified, cloud-based platform that allows enterprises to secure their applications from the first line of code to deployment in the cloud.
Get everything your enterprise needs to integrate AppSec across every stage of the SDLC and build a successful AppSec program.
FUSION
Correlate multi-engine scans automatically to prioritize finding and fixing business-critical vulnerabilities
ENGINES
Learn more about Checkmarx SAST
Find out how Checkmarx SAST helps organizations prioritize and fix vulnerabilities faster.
Related Resources

White paper
A Guide to Modern API Security
Understand the challenges in securing your API footprint
White paper
The Checkmarx Approach to API Security
See how a shift-left approach to API security can help you secure shadow and zombie APIs

Blog
Speed & Security: Our Next-Gen SAST Engine
Checkmarx is the only solution that offers both speed and security in a single package, providing enterprises with the power and flexibility to secure their entire application footprint.

Video
What’s New in Our Next-Gen SAST Engine
Discover how you can take advantage of our next-generation SAST engine right away. You no longer need to choose between speed or security – your enterprise can have both.
Video
Tailored presets and custom queries
Get tips on fine-tuning your AppSec solutions to boost alert fidelity and build developer trust