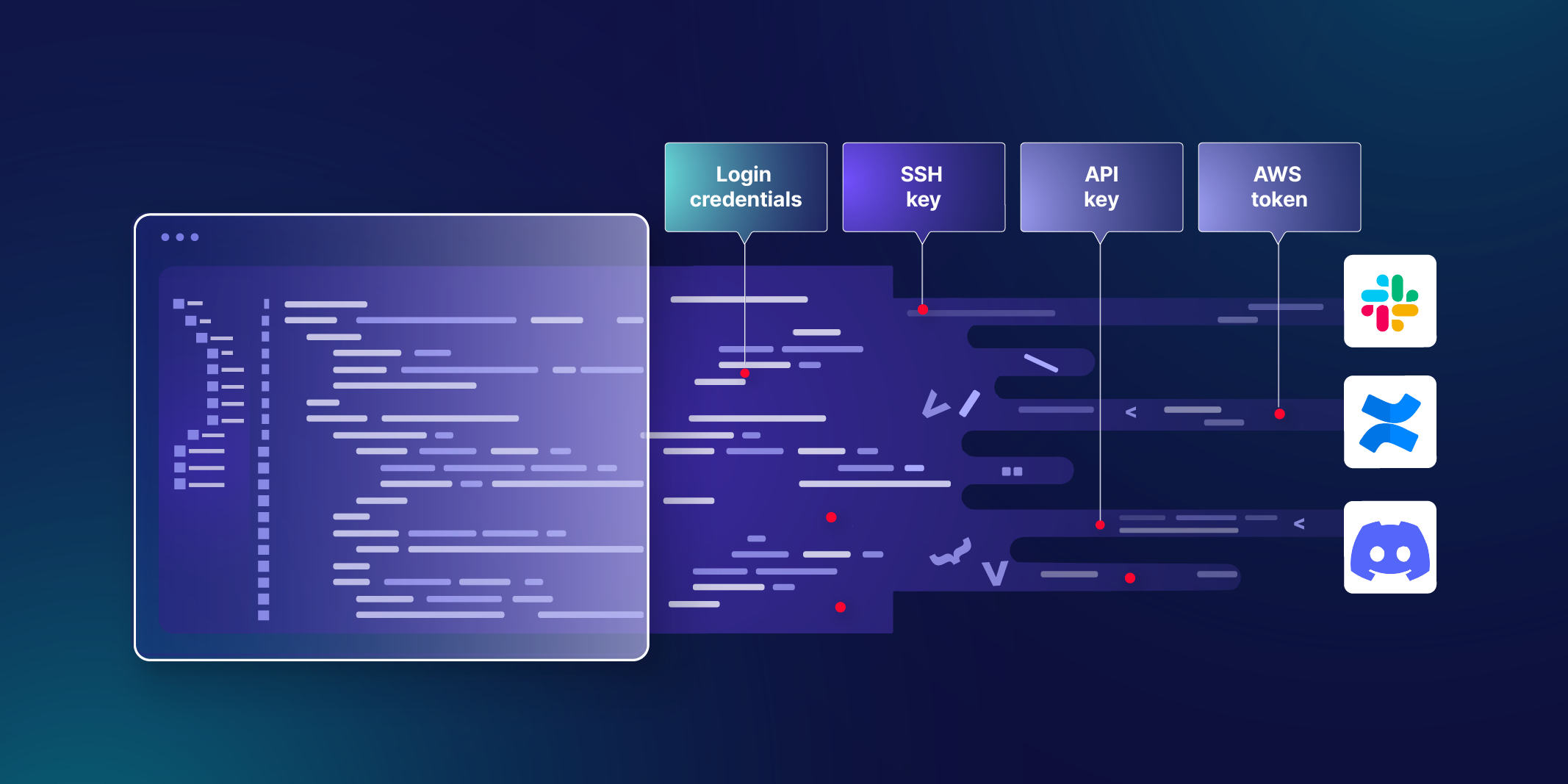
Blog
Checkmarx Blog
Expert insights, thoughtful essays, opinionated views, and more. Find them all here.
Scan Smarter (and more accurate) with Checkmarx
Findout what the industry’s most accurate flexible and frictionless solution can do for you.